Key Changes required to
Protect Your Federal Financial Aid
For higher education institutions offering financial aid to students, the Gramm-Leach-Bliley Act (GLBA) means an institution is required to meet compliance standards pertaining to the security and protection of financial information, and to provide transparency related to how personal information is used and shared. Failure to meet these standards carries significant risk for institutions, including restrictions or loss of eligibility for Title IV funding. In July 2024, Edge security, privacy, and compliance experts hosted a webinar focused on key changes to GLBA compliance requirements, how these revisions increase the compliance burden for many organizations, and key steps for meeting the new standard and maintaining compliance to receive federal financial aid support.
GLBA Compliance
In the last 10 years, GLBA has become increasingly integrated with higher education and higher education technology. This act regulates the protections that must be in place to protect student financial information for institutions that issue or handle student aid through Title IV programs, or who use the Student Aid Internet Gateway system. Since 2018, the Office of Federal Student Aid (FSA) at the U.S. Department of Education has encouraged higher education institutions to work toward adopting NIST SP 800-171, and later in 2020, has indicated this may be included in future compliance requirements.
More recently in May 2024, NIST updated the content of SP 800-171 standard to Revision 3, changing the specific controls required to achieve compliance. These changes mean that higher education institutions will need to re-assess compliance if they are currently implementing an earlier revision of NIST SP 800-171 to meet the upcoming GLBA requirement. “For member institutions using the EdgePro virtual CISO (vCISO) service, they are already aware of the GLBA requirements, and we have strategies in place to bring their organization onto the NIST 800-171 standard,” explains Dr. Dawn Dunkerley, Edge’s Principal vCISO. “The changes for Revision 3 will change ongoing work and will require updates to policies and procedures that are already developed.”
“Other institutions that are currently compliant with GLBA may not yet be working towards compliance with NIST SP 800-171,” continues Dunkerley. “This can be a great opportunity to be proactive and receive an assessment to identify any gaps to NIST SP 800-171 Rev 3 compliance. The EdgePro vCISO can be another asset to help with documentation, make recommendations for technologies, and create processes for immediate adoption, implementation, and operational improvements within the organization.”
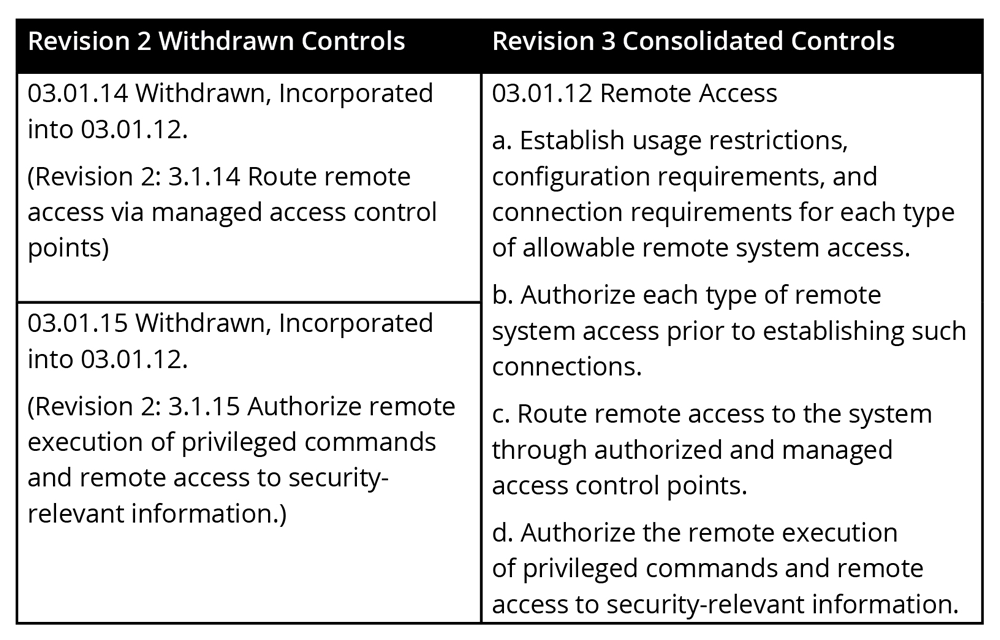
Withdrawn and Consolidated Controls
Even those institutions who are already tracking compliance with NIST SP 800-171 will need to make adjustments in order to stay compliant for the upcoming GLBA requirement. Revision 3 makes several changes that will impact institutions in both administration and in substantive control requirements. On the administrative side, there will be updates required to domain and control numbering schemes, titles, and specific language. “Each control was renumbered, so if you have a system security plan, it will require touch labor on each specific control,” says Dunkerley. “Several controls have been withdrawn and some existing controls have been consolidated and combined with other existing controls. There are also three new domains added, including nine individual controls that focus more on depth and proving control implementation, versus simply defying activities that should be done. The framework now has a helpful supplemental document that is a guide for assessors and allows an institution to look at each control and ask questions such as, how would an assessor test me on this; what is the interview they might conduct; what is a possible technical test; and what artifacts would they be looking for from a documentation perspective?”
All of the controls listed in the new revision have been re-numbered, re-titled, and the descriptions of requirements have been expanded to make requirements clearer. Any documentation that specifically references the NIST SP 800-171 Revision 2 controls will need to be updated in kind, and updated control descriptions will need to be reviewed to ensure that the control implementation in practice matches the clarified descriptions. “The updated and clarified control language may help institutions implement controls more effectively and the assessment guide is helpful for understanding how each would be tested,” says Dunkerley. “Institutions that have already implemented these controls should decide whether to keep each control in place or remove the relevant requirements from policies and enforcement practices.”
“The new substantive controls changes focus on not only performing activities to achieve compliance but proving that you do. This may include documented processes, logs, interviews, or a technical analysis with an auditor. By following the supplemental document, an institution can get into an auditor’s mindset as they’re reviewing their policies and procedures. Navigating the new landscape of GLBA compliance can be challenging, but we are here to help institutions understand these requirements, develop strategies for safeguarding financial information, and ensure compliance every step of the way.”
— Dr. Dawn Dunkerley
Principal vCISO, Edge

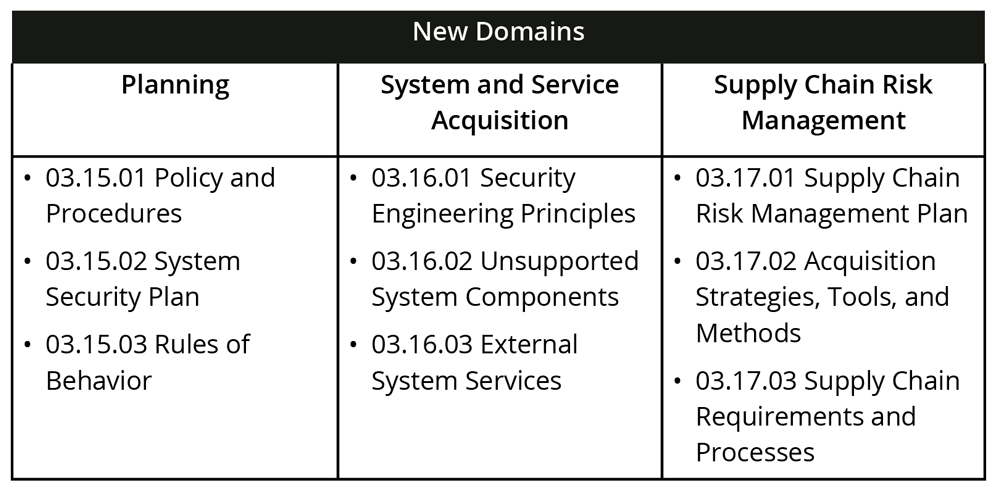
New Domains
Three new domains have been added in Revision 3, which will require new controls to be implemented that were not tracked in previous versions of the NIST SP 800-171 standard. “One of the more exciting pieces in these updates is the addition of new domains,” shares Dunkerley. “They are planning, system and services acquisition, and supply chain risk management. There can be several policies and procedures that fall underneath each of these, but the two main artifacts specific to this particular framework are the system security plan (SSP) and the plan of action and milestones. The SSP is a living document that shows where an organization is in compliance with the control set. There is a SSP template that shows each control, and an institution is either compliant, non-compliant, or it doesn’t apply.”
An institution can use this document to track progress and determine which actions are required to become compliant. The new set of controls for system and services acquisition is associated with following proper practices and procedures for internal development. “We must ask ourselves; how do we engineer security into the things we are building?” says Dunkerley. “If we have a situation where something is not supported by the vendor, what are the practices that are required to minimize the risk to ourselves? How are we dictating to an external provider what security requirements they are required to follow and how will they be held accountable? Each institution must have vendor risk management procedures in place that have active monitoring of their critical vendors.”
Designed for higher education to measure vendor risk, the Higher Education Community Vendor Assessment Tool (HECVAT) is a questionnaire framework that helps assess the information, data, and cybersecurity policies that are in place to protect sensitive institutional information. “Edge likes to use this tool in conjunction with other automated tools before a vendor is brought into our ecosystem,” explains Dunkerley. “We look for a company to share their security practices and documentation, network diagrams, risk assessment results, and how they mitigate any vulnerabilities.”
Substantive Control Changes
In response to the latest trends in the cyber threat landscape, 11 new controls have been added to the existing domain structure and should be implemented to work towards compliance and improve institutional security. These controls may require new policies, documentation, and practices to achieve compliance. “The new substantive controls changes focus on not only performing activities to achieve compliance but proving that you do,” explains Dunkerley. “This may include documented processes, logs, interviews, or a technical analysis with an auditor. By following the supplemental document, an institution can get into an auditor’s mindset as they’re reviewing their policies and procedures. Navigating the new landscape of GLBA compliance can be challenging, but we are here to help institutions understand these requirements, develop strategies for safeguarding financial information, and ensure compliance every step of the way.”
The EdgePro vCISO provides independent and objective input to ensure that your security posture is on track, identifies areas of necessary improvement, and supports areas where you’re already in compliance. To learn more about this service or conducting an assessment, visit njedge.net/solutions-overview/vciso.


